Some people use a passcode on their iPhones simply to prevent their kids from mucking around with it or accidentally calling the police. Others use it for actual security reasons — because there’s private information on your phone that you wouldn’t want a stranger to have access to. If you’re in the latter group, hopefully you use a passcode that isn’t easy to guess.
Daniel Amitay, developer of the Big Brother Security Camera app (now removed from the App Store), added some code to the app to record user passcodes anonymously. Here are his findings.
Naturally, 1234 is the most common passcode: mimicking the most common internet passwords. To put this into perspective, these 10 codes represent 15% of all passcodes in use. Most of the top passcodes follow typical formulas, such as four identical digits, moving in a line up/down the pad, repetition. 5683 is the passcode with the least obvious pattern, but it turns out that it is the number representation of LOVE (5683), once again mimicking a very common internet password: “iloveyou.”
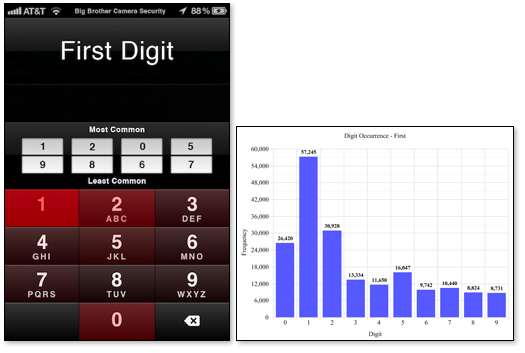
The passcodes are actually those entered on the Big Brother Security app, which shows a similar interface to the the iPhone passcode screen. Basically, the app replaces the iPhone passcode screen and takes a picture of hooligans who enter incorrect codes. So there’s an assumption that the two correlate, but the assumption seems reasonable.


 Visualize This: The FlowingData Guide to Design, Visualization, and Statistics (2nd Edition)
Visualize This: The FlowingData Guide to Design, Visualization, and Statistics (2nd Edition)

I don’t know if the assumption that a passcode attempt by a hooligan and codes actually in use correlate. Someone who isn’t bright enough to recognize that the Big Brother app screen is NOT the iPhone lock screen probably doesn’t own an iPhone. The codes captured by BB had nothing to do with actual codes in-use on iPhones.
These aren’t the incorrect passcodes though that random people entered. These were the codes that actual iPhone users with the app had in place.
http://amitay.us/blog/files/big_brother_removed_from_app_store.php
“I think I should clarify exactly what data I was referring to, and how I was obtaining it. First, these passcodes are those that are input into Big Brother, not the actual iPhone lockscreen passcodes. Second, when the app sends this data to my server, it is literally sending only that number (e.g. “1234”) and nothing else. I have no way of identifying any user or device whatsoever. “
Wouldn’t it be a good guess that most of the numbers entered are the correct codes? How often does a stranger try to unlock someone else’s phone, and wouldn’t most people disable the iPhone lockscreen instead of having to enter a code twice? I don’t have an iPhone, so I’m only guessing… but it seems like there should be a link between the two (again, just a guess :).
I think the purpose of the app was FOR strangers to enter codes. The iPhone’s lock screen can’t be customized or overwritten, and 3rd party apps can’t lock the phone.
It’s interesting data nonetheless! From your viewpoint, you could say that most iPhone owners use simple passcodes. From mine, you could say that most potential iPhone thieves think that most iPhone owners use simple passcodes.
Okay, I am clueless. 1998?
“Interestingly, 1990-2000 are all in the top 50, and 1980-1989 are all in the top 100. I would interpret this occurrence as a subset of users that set their passcodes to the year of their birth or graduation.”
http://amitay.us/blog/files/big_brother_removed_from_app_store.php <– I'm not surprised! Harvesting passcodes was not the brightest of ideas :\